

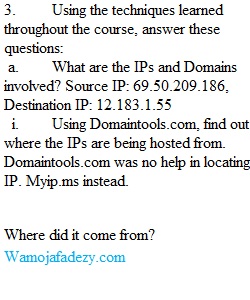
Q Examining a Malicious PCAP 1. Open a terminal and type “cp /opt/samples/fake_av.pcap /home/so/Desktop/” and press enter. You should see the file “fake_av.pcap” on your desktop. 2. Double click the file to load it in Wireshark or load into Security Onion with “so-import-pcap”. 3. Using the techniques learned throughout the course, answer these questions: a. What are the IPs and Domains involved? i. Using Domaintools.com, find out where the IPs are being hosted from.b. What is the name of the executable that was transferred to the victim machine? c. Where did it come from? i. Looking at the first packet, is this is the first or second stage of infection? Why?
View Related Questions